Category: Tips & Tricks
-
SSL vs TLS: Understanding the Differences
When it comes to securing data transmission over networks, SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are two commonly used cryptographic protocols. While they share a similar purpose, there are significant differences between the two. In this article, we will explore these differences and understand why TLS has become the standard protocol for…
-

Hashing: The Key to Secure Data Integrity
Introduction In the digital age, data security has become a paramount concern. From passwords and personal information to sensitive documents and financial records, protecting data from unauthorized access and manipulation is crucial. One of the fundamental tools used to ensure data integrity is hashing. In this blog, we will explore what hashing is, why it…
-
Encryption: Safeguarding Data in the Digital Age
Introduction In today’s interconnected world, data security is paramount. Whether it’s personal information, financial transactions, or confidential business communications, protecting sensitive data from unauthorized access is crucial. Encryption, a method of encoding information, plays a pivotal role in securing digital communications and has a rich history dating back centuries. In this blog post, we will…
-

Hashing vs Encryption vs Encoding
1. Hashing: Explanation: Hashing is a one-way function that produces a fixed-size hash value from an input. It is primarily used for data integrity and verification. Hash functions are designed to be computationally easy to calculate the hash value, but nearly impossible to reverse to the original input. Example: Let’s say we want to calculate…
-

Understanding the OWASP Top 10: A Comprehensive Guide
Introduction The OWASP Top 10 is a globally recognized document that highlights the most critical web application security risks. This blog aims to provide a comprehensive understanding of the OWASP Top 10, including its purpose, the specific vulnerabilities it covers, real-world examples, and strategies for mitigating these risks. What is OWASP? The Open Web Application…
-
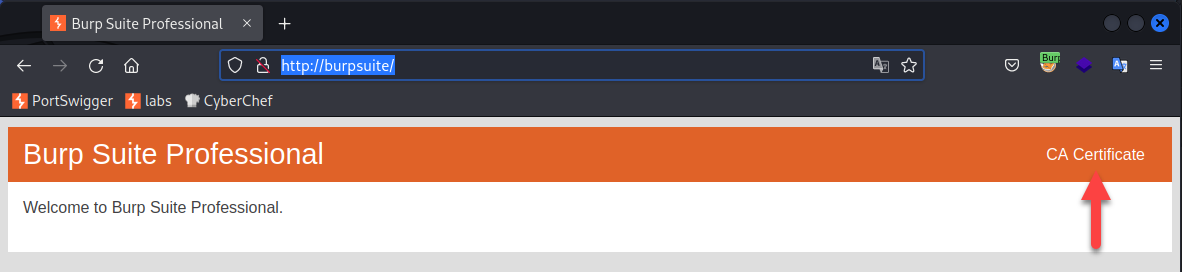
Installing Burp’s certificate in Firefox
If you are a security professional or a web developer, chances are you have come across Burp Suite – a powerful web security testing tool used to identify and fix vulnerabilities in web applications. One of the essential steps to use Burp Suite effectively is to configure your browser to trust its CA certificate. This…
-

Decrypting Locally Stored Firefox Passwords
Welcome to our blog post on decrypting locally stored Firefox passwords! In this article, we will explore the process of decrypting passwords saved in Mozilla Firefox’s local storage. Please note that this information is intended for educational purposes only. Disclaimer: Decrypting passwords without proper authorization is illegal and unethical. This article is meant to increase…
-

Decrypting Locally Stored Google Chrome Passwords
Google Chrome, like other browsers, stores all saved passwords locally. The encryption key and the saved passwords are stored in binary format, accessible to the device owner. While encrypting and storing passwords is a good security measure, it raises concerns about the potential extraction of plaintext passwords by hackers. This prompts us to question whether…